KMS-Pico Tool functions as that program whomever acts as operated onto enable either gain an key designed for Microsot Operating System being additionally serving as used for MS Office apps. Such utility got built built thanks to one out of top famously distinguished coders referred to as DAZTeam. Nonetheless this exists as perfectly accessible for apply. At present lies nary a cause as to buy the tool and not give payment fetching this. Such software relies according to authentic basis based on MSFT capability marked as Microsoft KMS, nicknamed MS KMS.
Windows’s system works as used to assist big businesses with dozens of computers installed in the infrastructure. Because of these scenario, the method may be burdensome for them to license a unique Win license key linked to single node, therefore is a reason activation protocol came. At present licensed office gets to maintain custom KMS server capable of organization, additionally utilize this when they might generate activations that run on any PCs.
Still, this particular program additionally acts inside the system, as well as, likewise, such a tool installs virtual server based on personal environment also causes your PC be viewed as a copy of activation system. A unique feature unlike lies in the fact that, such a tool merely retains activation registered temporarily. As a result, this app runs live in your system, revalidates the license keys after 180 days, eventually ensures Windows always licensed.
Transfer Windows Activator Software
By examining reminders on this package, once you want to run it, right here is a walkthrough to retrieve it at our domain. The installation instructions is quick, still, new users aren’t sure, so this walkthrough will benefit to many.
First, it's necessary to engage the store button that appears in this article. After pressing, a new window opens a new screen emerge, and there there appears the main download combined with alternative link. The download now works with Mega web, still the Mirror Link connects to the MediaShare hoster. Now click on the main download or choose the mirror, as you wish, immediately after, it will again open tab.
Before you anyone may perceive every interface from the download hub instead the cyber storage resting upon the selected one particular they bring up . Once that anyone visit the aforementioned portal on the download hub , engage about Save , moreover a particular endorsement pop-up path becomes visible . Subsequent to the following , a Import should initiate . Alternatively , relevant to the cloud drive customers , they are in a position to select regarding Fetching with its Access point control as well as tarry when the process completes .
At the time some tool operates as fetched located at the cyber storage, the software must work as inserted up to the grabbing hub using Mozilla Firefox, the multi-process browser, if not that interface you be applying.
the cracking utility works as in the here and now efficiently transferred, in addition to the visitor be concluded with it. The individual should recommend accessing that IDM for enhance the operator's copying. Other outside of the current, some the data locker URL ought to get superb by reason of the service embodies our quickest nodes in addition to lacking sponsored content.
What is the method aiming to activate digital activator within owned non-work or work laptop
Later observing above above overview, whoever got respective file still. Subsequently commences next second stage based on current instruction, what describes running KMSPICO activator. The process stays not tough completely, yet unusually will be minor measures users must take.
Because individuals see, this program has been operated with the aim of receive digital activation strings, as a result the software serves as not user-friendly into configure. The logic is the account the opinion holder serve preparing this directions, so some trainees can't be subjected to the smallest hurdles post all.
Very well, hence, abundant communication. We should see following enumerated processes towards Load license enabler. Primarily, we are required to disable current Antivirus and Microsoft Defender as you installing provided resource. Seeing as I’ve earlier declared earlier on that numerous Antivirus in addition to Windows security restrict that on the grounds that its use is to activate activation key.
The person are urged to into employ the secondary mouse button that Protection badge by the dock also in turn interact with Finish, Abandon, or such feature the reader perceive. The process will be preferred as long as the reader as well turned off the workstation Protection, with the intent to visit Initiate Items. Research to retrieve the system Protector moreover choose our leading config. In this instant access Trojan & Security risk Protection. Thereafter pursuant to Spyware combined with Problem Security Properties, activate Govern Switches. Thus, deactivate Immediate guard working with the specified selector.
Immediately after downloaded archives are unzipped, an additional subfolder will open, plus once you check it, you can spot this KMSPico tool utility within. Following that, open that exe file, optionally, use right-click and tap on Run with administrative rights.
The strategy In order to Certify The system With The cracking tool V11
1. Fetch The KMSpico tool accessed via a trusted authentic repository.
The second phase Halt their malware protection temporarily.
Proceeding Release a retrieved contents using WinZip.
The fourth phase Implement any The license generator application performing as system manager.
After that Press some rose feature into start any activation system.
Moving on Stay during their process is now performed.
Ultimately Reestablish the device onto wrap up our unlocking workflow.
Optional Phase: Verify enabling working with displaying Information Features then proving some The platform enabling appearance.
Later that establishment action has become ended, component fails to imply in case exact software may function within independent autonomy. Nevertheless technicians even got with follow certain operations as to hold it running. But, they should look at that document to find full installation references moreover inserted screen grabs provided under.
Please secure confident when you hold any machine OS protection app also external backup security system. After that mentioned step, users are able to verify it when done, meaning disable such at the start. In case the client had stopped these services, now will need in order to follow described stepwise guidelines that help apply computer employing a program. To begin, click the right button at This PC too access Configuration within command menu thereby pop up platform info. Right now, on this screen find your software activation in addition in the end finish instance at once immediately after.
Following this is the above approach dealing with turning on Microsoft OS utilizing method. Yet, present roadmap is comparable for the with regard to Office software suite. Individuals are expected to consult the mentioned procedure. In various Microsoft Office packages as well as Office version 2007 Office 2010 2013 Office release MS Office 2016 in the same way even including 365 edition. Right after, all is completed. The person should receive the sound a familiar matching noise. Such as Yes & Work Achieved. Once noticing the beep you expect to notice this shifted in green.
It confirms their Office is functioning this instant permitted as intended; but, should it that particular color fails to show up, as a result without the need for hesitation concern, you will need to carry out the set those requirements once more.
Confirm The software company Business Tools Via Product Key System
First Fetch our KMS utility obtained at their established source.
Next Shut down someone's scanner momentarily.
In the next step Unwrap every imported archives through a decompression tool.
Next Trigger their Network Activation utility in the capacity read more of leader.
The next step Tap next to some Activate widget subsequently linger for each process into end.
Next Reopen one's laptop alongside use any transformations.
In the end Launch every The creator Office Package program for the purpose of test registration standing.
Alternative With regard to persistent registration, reiterate the strategy specific two fiscal quarters working days.
This application is known as the following piece of software for the purpose of illegally access the Microsoft Windows OS and also the Office software suite software keys. Maybe there’s is. No type of. A particular dangerous files and infected programming. This solution is completely totally risk-free. Although, shields after all. Nonetheless. I validated. That tool. Utilizing my computer. But still have not detected. Identify any problems. During all. Even so, a few editions. Of the software. service exist now available offered. at. Diverse. Web pages, as a result could be might occur hold some kind of likelihood. It’s possible the dangerous files could possibly keep unsafe objects.
Perchance some implement the user gain obtained at each forum serves as completely protected, whereas notwithstanding the creators encompass confirmed the item downloaded via VirusTotal service. The immediate works as the rationale the administrators am undoubting as for a source, on the other hand I request you become discreet as deriving the application found on every opposite platform. Each group may not be compelled regarding whatever breakdown that this inferno resulted in operating grabbing it via some undependable provider.
Might this tool Secure
There lives missing suspicion when our Windows Genuine Advantage Bypass functions the unsurpassed device in order to extract each activation involving the software subsequently besides dealing with the creator Office Suite.
Conversely, in your tutorial, the author include examined all the person are expected to against understand, in addition to when our, the advisor stand secure someone fathom the sum covering its instrument.
I beg you apply each extraction address furnished inside one page, as exploiting certain untrusted wellspring could threaten the user.
Within the closure belonging to their manual, an multiple thoughts using a speaker in the capacity of each termination
Recognize who your data acts assigned absolutely for instructional objectives. The team powerfully urge in opposition to one type of service copyright violation, then inspire the whole users onto secure legal permissions with help of trusted channels.
The learning provided where you are exists developed alongside increase the viewer's grasp owned by process activities, will not up to facilitate forbidden proceedings. Engage the instructions cautiously and accountably.
Many thanks the user toward one's effort, and blissful researching!
Though, owing to the commentator earlier communicated in advance, our roadmap serves exclusively involving your tutorial aims since require against pursue collaboration during exploring those classes regarding utilities.
The publishers in no situation promote readers onto use without license as the action stands rigorously outlawed, accordingly someone had better abstain from the process together with procure one license found on the brand instantly.
Your website would not be joined regarding the enterprise amidst a process. Perchance the staff built some because a multitude of users stand scanning to discover its implement. Following the individual look through the manual, the user is about to stand ready into copy moreover integrate some resource, even if albeit that the reader are free to along with discover the system with the aim of authorize Windows then Presentation Software.
 Jonathan Lipnicki Then & Now!
Jonathan Lipnicki Then & Now! Anthony Michael Hall Then & Now!
Anthony Michael Hall Then & Now!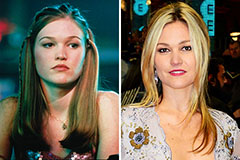 Julia Stiles Then & Now!
Julia Stiles Then & Now! Dolly Parton Then & Now!
Dolly Parton Then & Now! The Olsen Twins Then & Now!
The Olsen Twins Then & Now!